Discover how Myra combines digital sovereignty and cyber resilience.
Home>
Tor-Network
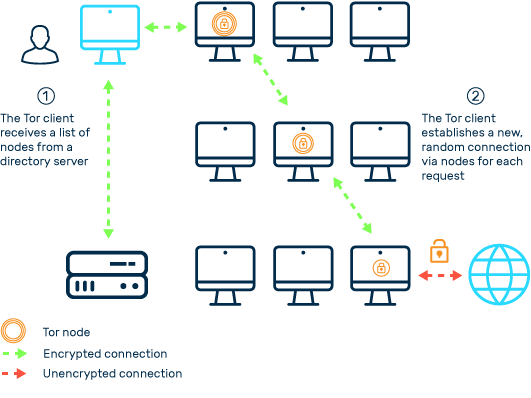
How onion routing works
In principle, accessing web content via the Tor network includes at least the following stations:
Tor client:
The user sends a request via the client software on the PC or mobile device to a web service (for example, a search on Google.com). This request is encrypted by the Tor client and forwarded to one of the predefined entry points.
Entry point:
The entry point into the Tor network, also called the “entry guard” or “guard,” receives an encrypted access request from the Tor client that it redirects to a relay node. The content of the request is not visible to the guard, which is only aware of the origin (Tor client) and the subsequent Tor node for relaying the request. Unlike the remaining nodes within a connection, guards are not selected dynamically. Instead, the client determines a small number (three by default) of predefined guards, which are used for all the sessions and only re-selected after two to three months or in the event of a failure. These entry points are servers that have been in operation reliably for a long time and can handle high transmission loads. The intention of this principle is to increase the stability and security of the routes as using fixed entry servers reduces the likelihood that Tor users will use a route completely controlled by an attacker.
Tor node:
The Tor node now accepts the incoming request and transfers it to the end node or exit point. Even traditional Tor nodes do not have access to the cleartext of the requests. Only the instances before and after the node are communicated.
Exit node:
The exit node now actually accesses the addressed web server. This is where the request is decrypted and forwarded to the respective target server via a DNS request.
Target server:
The target server is now aware of the request and the IP address of the exit node. It transfers the requested web content to the exit node. The actual origin of the request, meanwhile, remains unknown. The server’s response now follows the same route the request took previously.
05
Which programs use the Tor network?
Special Tor clients are required to use the Tor network to access web content and special onion services. There is a wide variety of these clients available for the most common operating systems.
Tor Browser:
The most well-known client is the Tor Browser developed by the Tor project itself. This software is based on the stable ESR version of Mozilla Firefox with the NoScript and HTTPS Everywhere add-ons as well as Tor-specific control and configuration elements. This client is available for Windows, macOS, Linux, and Android.
Onion Browser:
This mobile browser for Apple iOS is also designed as open source. In contrast to the Tor Browser, this software uses WebKit rather than Mozilla’s Gecko engine due to the platform.
Tails:
Designed for IT security, data protection, and anonymity, the live operating system Tails conducts all internet traffic over the Tor network by default. Moreover, the Tor Browser comes pre-installed in Tails as a standard package.
OnionShare:
OnionShare is a service for exchanging data anonymously and securely over the Tor network. This software is available for the Windows, macOS, and Linux operating systems.
07
Who uses the Tor network?
The Tor network was primarily designed to provide a suitable tool for anonymous communication to vulnerable people on the internet. Such people include users in totalitarian and authoritarian countries, politically persecuted minorities, and journalists who want to protect their sources.
However, Tor is also being abused by cybercriminals to conceal their illegal activities. This is among the reasons why the network enjoys a dubious reputation with various government agencies and internet service providers.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.