Discover how Myra combines digital sovereignty and cyber resilience.
You're in Good Company When You Choose Myra











![]init[](https://www.myrasecurity.com/assets/79302/1674209677-init_logo_farbe_190x74-1.png?auto=format)














We Tackle Your Toughest Security Challenges

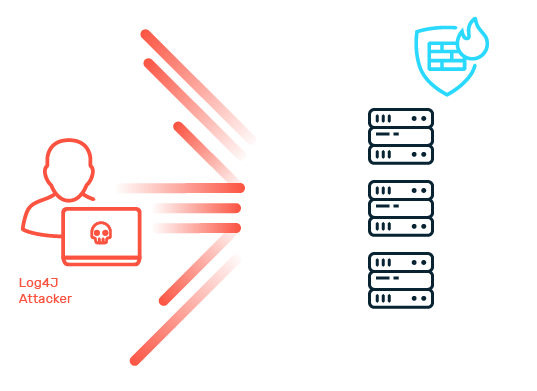
No Protection Against The OWASP Top 10
Lack of safeguards leaves apps open to SQLi, XSS, and CSRF. Attackers exploit these flaws to steal data, hijack sessions, and take control.

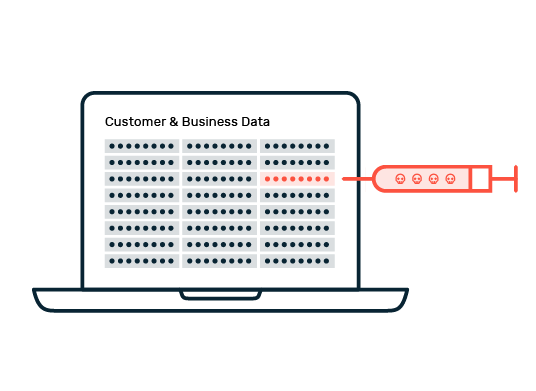
Inability to Mitigate API Threats
Weak API security makes data vulnerable to injections, exploits and leaks. Attackers take advantage of faulty authentication and missing protection measures, which leads to interruptions.

Complex and Disruptive Implementation
Difficult setups and compatibility issues can cause delays. They also increase costs and disrupt operations. Plus, extra hardware may be needed.

Overwhelming Compliance Challenges
Meeting strict regulations like NIS-2, DORA, and GDPR is tough without certified solutions. This gap can expose organizations to legal risks and data breaches.
Key Benefits of Myra's WAF

Protection for Your Applications
Myra WAF provides protection against the OWASP Top 10 vulnerabilities. We block more than 8 million malicious layer 7 requests on average per customer per year.

Managed Service with Expert Support
Myra's managed WAF service helps protect your web resources. Experts review your needs and tailor rule sets just for you. They also offer ongoing support and optimization.

Get up and Running in No Time
Get started right away with no extra hardware or complicated setups. Myra's Web Application Firewall works seamlessly with your existing infrastructure.

Ensure Full Compliance with Key Regulations
Myra itself is NIS-2-, DORA-, and GDPR-compliant and can help you meet regulatory requirements, especially in highly regulated sectors.
Certified Security You Can Rely On
Intuitive WAF Management
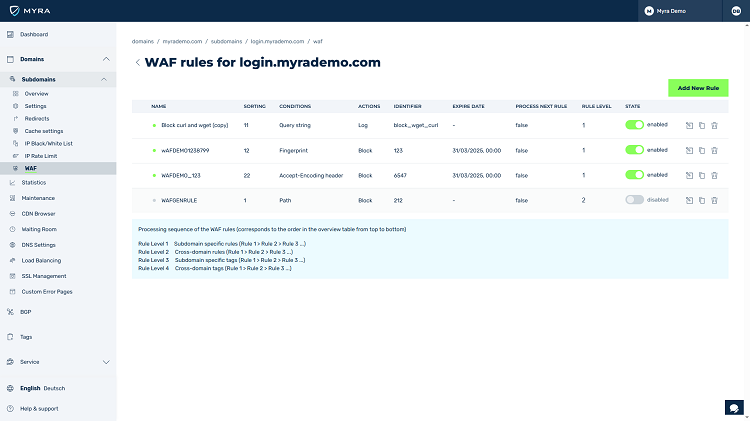
All WAF Features

Versatile Usage
Whether you run your web applications in your own data centre, at a hosting service provider or in public/private cloud instances, the Myra WAF serves as an upstream protective wall in all deployment scenarios – efficiently and cost-effectively.

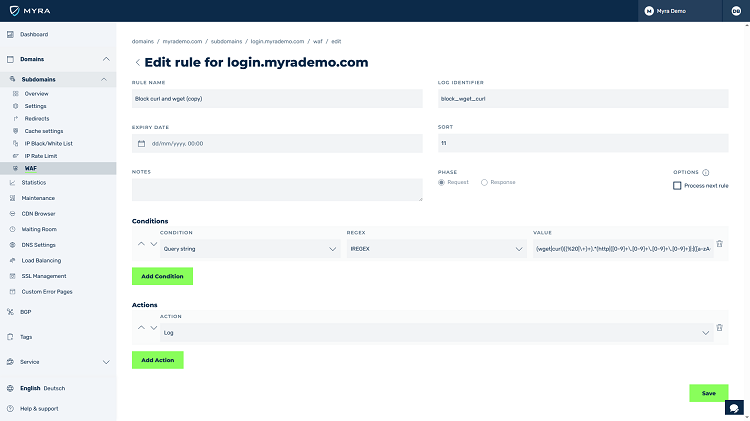
HTTP/S Request Filtering
Filtering of HTTP/S requests is ready to use with the Web Application Firewall from Myra and is almost infinitely scalable. WAF rules are defined based on simple comparisons or regular expression (regex).

Managed WAF
If you wish, the Myra experts can support you in analysing your web resources and creating customized rules – benefit from the best possible protection without sacrificing productivity.

Custom Error Pages
The Myra WAF supports the display of individual error pages that are adapted to your corporate design. Provide your customers with concrete added value through further details and maintenance information.

Comprehensive Rule Sets
WAF rules managed and constantly updated by Myra protect against the most frequent attack risks (OWASP Top 10) and zero-day exploits. The defence against XSS, CSRF, SQL injection, and directory traversal is provided by included rule sets.

Header Modification & Rewriting
The Myra Web Application Firewall allows header/response rewriting without adjustments to the application. Likewise, adjustments to the headers in request and response phases are possible.

Configuration via API
You can either configure the Myra WAF via an easy-to-use web interface or control the protection solution completely via an API in your existing system landscape.

Alerting
Stay informed – the Myra Web Application Firewall automatically informs you about incidents via freely configurable alerting by email, API calls or SMS.

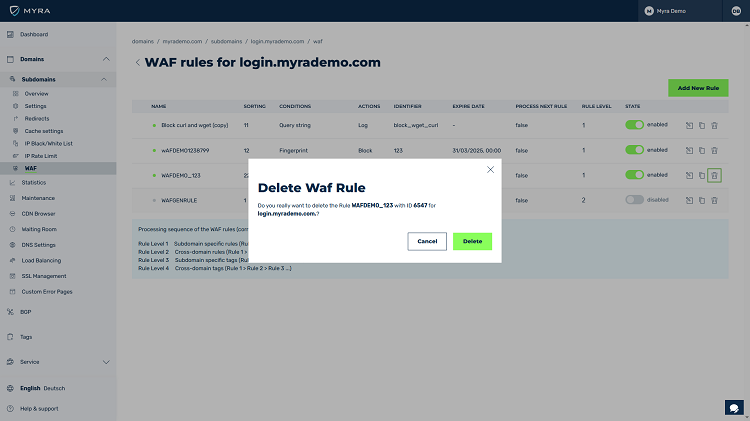
Web-Based Rule Management
Myra offers web-based rule management for pre- and post-origin traffic. This gives you complete control over all rule settings, which include numerous conditions and actions for the request or response phase.
Security You Can Count On

bots were fended off in DDoS attacks as part of pentests.

malicious Layer 7 requests are blocked by Myra on average per customer per year.

Service Level Agreement (SLA) for service availability.
“97 % of DACH companies reported at least one cyber incident in the past year.” - Deloitte Global Future of Cyber Survey 2024
Myra Protects Your Web Applications from a Wide Range of Threats
Protect your web applications from modern attacks
Book a demo now and learn more about the Myra WAF.
Hundreds of millions of HTTP requests can be processed per second to provide protection against the latest attacks.
Guaranteed availability with up to 99.999% SLA.

Legally GDPR-compliant and made in Germany.
Over 500 companies from highly regulated sectors such as finance, government institutions, healthcare, and critical infrastructure place their trust in us.
"Myra puts us in a solid position in terms of cybersecurity, web-performance and compliance."
– Hendrik Hoffmann, Division Manager Technology at Sparkassen-Finanzportal GmbH

Web Application Firewall – Frequently asked questions (FAQ)
WAF security solutions protects web applications from attacks via the Hypertext Transfer Protocol (HTTP/S). Unlike classic firewalls and intrusion detection systems (IDS), a WAF service examines communication directly at the application level. Incoming requests and the responses of the web server are examined and checked for suspicious patterns. Requests that are classified as harmful are blocked by the protection solution – this ensures protection of the applications without the need for adjustments to the application itself.