New: Flexible service plans for Myra WAF. Learn more!
Home>
SYN Flood
02
How Does a SYN Flood Attack Work?
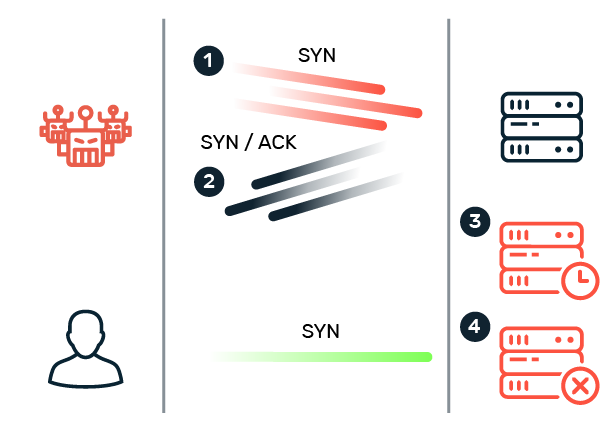
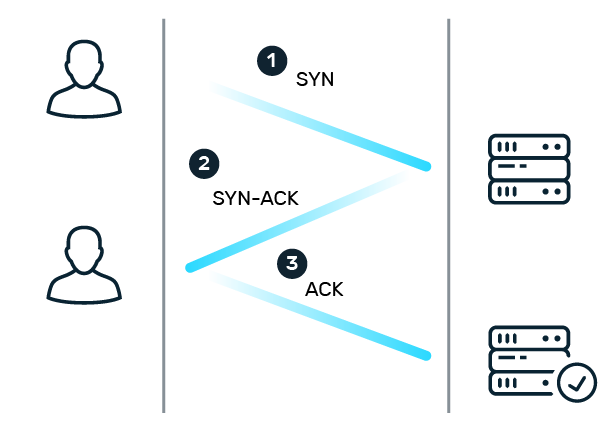
When a client and server want to establish a TCP connection, the process follows the so-called three-way handshake. The client first sends a SYN packet (from “synchronize”) to the server. The server responds with a SYN-ACK packet (from “acknowledge”). To successfully establish the connection, the client must now send a final ACK packet to the server to acknowledge the server's confirmation. If the client does not send the final ACK packet, a half-open connection is created in which resources are allocated on the server while it waits for the ACK packet.
In a SYN flood, the server is flooded with SYN packets and overloaded by the mass imitation of regular connection requests. The result: no new connections can be established and the server is no longer accessible.
What Types of SYN Flood Attacks Exist?
SYN flood attacks can be categorized into three main types:
Direct SYN Flood
A single attacker sends SYN packets from his own IP address. This attack method is not very effective and can be easily traced, which is why it is rarely used.
SYN Flood With IP Spoofing
The attacker uses spoofed source IP addresses to make tracing more difficult and to make it more challenging to differentiate between legitimate and malicious traffic.
DDoS SYN Flood
In this case, the attacker usually uses a botnet to send SYN packets from many different IP addresses simultaneously. This makes detection and defense much more difficult.
04
What Are the Dangers of SYN Flood Attacks?
SYN flood attacks pose a serious threat to the availability and performance of networks and server systems. The consequences of an unmitigated SYN flood can be severe:
The Security-as-a-Service solutions from Myra provide reliable protection for your IT infrastructure and web applications against SYN floods and other cyberthreats. Ensure the security of your critical business processes proactively, sustainably and legally compliant.
05
How Can Organizations Fend off SYN Flood Attacks?
To protect your organization from SYN floods, the following measures are recommended:
Use of an intrusion detection system (IDS) or a firewall: IDS and modern firewalls analyze data traffic in real time and recognize suspicious attack patterns such as SYN floods. They can automatically block harmful connections and alert the security team. However, this requires continuous adjustment of the blocking rules, which is both costly in terms of time and effort and requires the appropriate know-how.
Increasing the backlog queue: The SYN backlog contains the information for establishing a TCP connection. Increasing the capacity of the backlog queue allows more connections to be stored, giving the server more time to process requests and avoid overload. However, each entry in the backlog reserves a certain amount of memory, so this defense method is limited.
Recycling the oldest half-open TCP connection: When the SYN backlog limit is reached, the server closes the oldest half-open connection and deletes it from the backlog to free up space for new connections. However, this protective measure quickly reaches its limits when attack volumes are high.
Activating SYN cookies: SYN cookies prevent the server from reserving resources for half-open connections with every new SYN request. Instead, it generates a SYN cookie, which is sent back to the client as the initial sequence number in the SYN-ACK packet. Cryptographic hashing ensures that the attacker cannot guess the sequence number. The connection is only established and resources are only reserved once the client has responded with an ACK packet and the server has verified the validity of the cookie. This method provides protection against SYN floods, but can sometimes lead to a decrease in performance.
Use of Anycast networks: Anycast distributes incoming traffic across multiple geographically separate servers and data centers. This balances the load across different locations, increasing the resilience of the network and reducing the likelihood of server failure.
Use of dedicated DDoS protection solutions: DDoS protection solutions from specialized IT security service providers detect SYN floods and other threats from malicious traffic flows in real time and block malicious requests before they reach the target system. These solutions are highly scalable and can efficiently mitigate even severe attacks that exceed the network capacity of the affected infrastructure.