Discover how Myra combines digital sovereignty and cyber resilience.
Home>
SSL/TLS certificate
At one look
- 1. SSL/TLS certificate: a definition
- 2. How does SSL/TLS encryption work?
- 3. What information does an SSL/TLS certificate include?
- 4. What are the different types of SSL/TLS certificates?
- 5. What are the benefits of using SSL/TLS certificates?
- 6. How do businesses obtain an SSL/TLS certificate?
- 7. How much does an SSL/TLS certificate cost?
- 8. How secure are SSL/TLS certificates?
- 9. SSL/TLS certificate: What you need to know
04
What are the different types of SSL/TLS certificates?
SSL certificates are issued by official certificate authorities (CA). They verify the applicant and identify him as trustworthy. There are different types of certificates, which meet different requirements:
Domain Validation Certificate (DV-SSL)
With this certificate, the certificate authority checks the applicant’s right to use a specific domain name. DV-SSL certificates can be issued very quickly because the certificate authority does not require any additional company documents.
Organization Validation Certificate (OV-SSL)
In addition to the applicant’s right to use a specific domain, the certificate authority also checks some additional company information. A website with an OV SSL certificate shows the user more information about the operator of the website, imparting a greater level of trust.
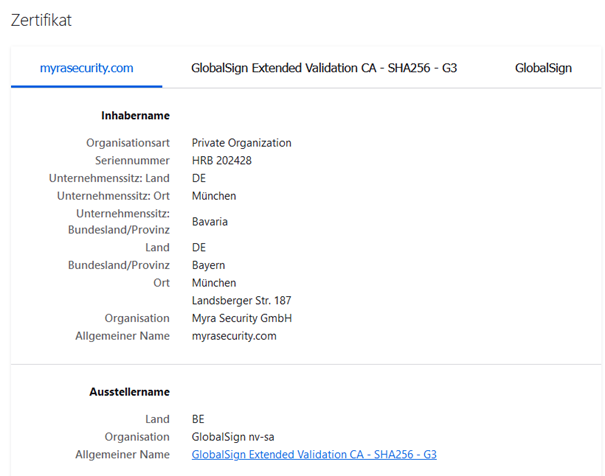
Extended Validation Certificate (EV-SSL)
In this case, the organization submitting the application is thoroughly vetted. The Guidelines for Extended Validation, published by the CA/Browser Forum in 2007, specify how the issuance process works. Organizations applying for this certification must verify, among other things, that the entity exists legally, materially and operationally, and has control over the domain.
Wildcard SSL/TLS certificate
A wildcard SSL certificate can be used to secure a base domain and any number of subdomains with a single certificate. This is usually much cheaper and less complex than having a separate certificate issued for each subdomain. For example, a Wildcard SSL certificate for the base domain example.com is also valid for login.example.com, mail.example.com or download.example.com.
06
How do businesses obtain an SSL/TLS certificate?
SSL certificates are generated and issued by a certificate authority. The trusted external organization also digitally signs the certificate with its own private key so that clients can verify it. After receiving the certificate, domain owners must install and activate it on the origin server. They should also ensure that the certificate is renewed in time to avoid the risk of it expiring and the encrypted domain becoming inaccessible.
However, this is becoming more and more of a hassle. In recent years, the maximum validity period of SSL certificates has steadily shortened. Initially, commercial certificates had a lifespan of up to five years, but in 2015 the maximum validity period was reduced to three years and finally to two years in 2018. Since fall 2020, SSL/TLS certificates have only been issued for up to 13 months. In addition, there are discussions about a general reduction of the validity period to a maximum of 90 days. Domain owners therefore have to worry about renewing their certificates at ever shorter intervals. Having a service provider automatically reissue the certificates can solve this problem.
08
How secure are SSL/TLS certificates?
Of course, even SSL/TLS certificates do not provide one hundred percent security. By exploiting vulnerabilities, attackers could prevent effective authentication and encryption via SSL/TLS. Entry points for possible attacks are:
Certificate authority
Although resellers and hosting providers perform security audits before accepting a certificate authority, there is still a risk that criminals will attack such an authority and create arbitrary certificates on its behalf.
Man-in-the-middle activities using arbitrary certificates
Intelligence agencies and investigative authorities can exploit vulnerabilities at certification authorities to eavesdrop on targeted connections using a valid certificate.
Fake certificate chains
By using special intermediate CA certificates, attackers can hack into encrypted connections and analyze their content.
Key generation
Some certificate authorities also handle the key generation. This poses a security risk, because the private key should be generated on the user’s own computer.
Compromise of certificates
If the private key is stolen without the certificate holder being aware of it, attackers can use the key to decrypt encrypted data.