Our WAF has a new user interface – for more intuitive and efficient use. Learn more
Home>
Slowloris
At one look
03
How is this different from traditional DDoS attacks?
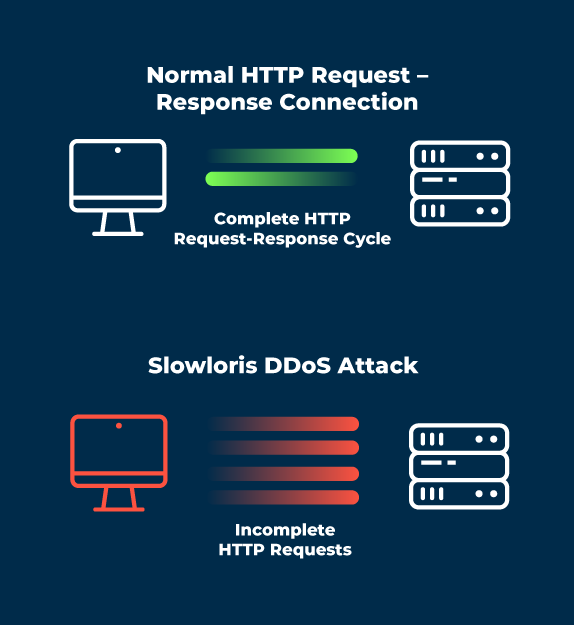
Compared to conventional flood attacks, a Slowloris attack uses relatively few resources on the attacker’s side. The load on the target server does not increase either; instead, it keeps too many connections open for too long without doing anything.
However, this is not a TCP DoS because a full TCP connection is established, not a partial one, but partial HTTP requests are sent. Thus, it is the equivalent of a SYN flood attack, only over HTTP. One example of the difference is that with two web servers running on the same machine, one can be attacked with DoS while the other web server instance remains unaffected. Slowloris is also NOT a GET request flooder. Slowloris only requires a few hundred requests at long and regular intervals, as opposed to tens of thousands on a continuous basis.
05
Who is impacted?
Slowloris is primarily a threat to web servers that use threaded processes and attempt to limit them to prevent running out of memory. Apache servers that allow direct access from the internet are sometimes affected.
Vulnerable systems include:
Apache 1.x
Apache 2.x
dhttpd
GoAhead WebServer
A notable Slowloris attack occurred in Iran while the software was still in its infancy. Slowloris was used against the Iranian government’s web servers during the 2009 presidential election. The attackers chose Slowloris over a traditional denial-of-service attack because such a traditional attack would have consumed a lot of network bandwidth, also harming the protest movement in the country. The attacks using Slowloris affected gerdab.ir, leader.ir, and president.ir.
06
Successor and variants
Since the release of Slowloris, several other programs have appeared that mimic how Slowloris works and provide additional features or run in other environments:
PyLoris
a Python implementation that supports Tor and SOCKS proxies
QSlowloris
a binary program that runs on Windows and has a Qt interface
dotloris
a Slowloris variant written in .NET Core
Slowloris.hx
an implementation written in the Haxe programming language
09
Myra’s solutions
The Myra Multi Cloud Load Balancer allows for the access volume to be distributed among any number of servers – even across multiple data centers. Redundant, highly available, and scalable. Myra DDoS Web Protection combined with the Myra Hyperscale WAF protects applications against impermissible and dangerous requests. The immediately scalable solution provides nearly limitless capacity for warding off requests.