Discover how Myra combines digital sovereignty and cyber resilience.
Home>
NIST CSF
03
How Is the NIST Cybersecurity Framework Structured?
The NIST Cybersecurity Framework was designed to be a living document that is refined, improved, and evolved over time to keep pace with technology and threat trends and to incorporate new lessons learned.
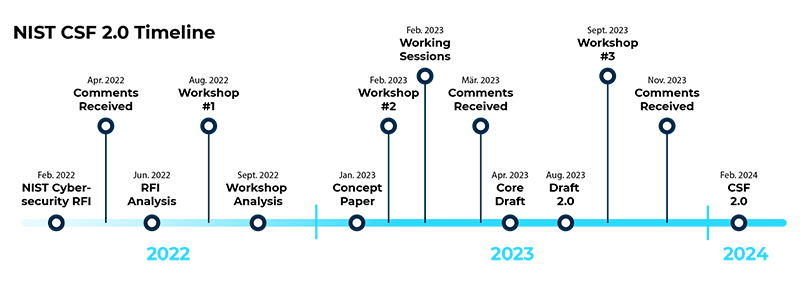
The first version of the Cybersecurity Framework (CSF 1.0) was published in 2014 and updated in 2018 (CSF 1.1). It was primarily aimed at operators of critical insfrastructure. In order to take account of the constantly evolving cybersecurity landscape and expand the range of applications, NIST has been developing a new version since 2022.
The NIST CSF 2.0 (PDF) was published in February 2024. It still consists of three main components: the Core, Organizational Profiles and Tiers. One new aspect is the greater consideration of topics such as cloud security, supply chain risks and threats associated with artificial intelligence (AI) and the Internet of Things (IoT). CSF 2.0 also focuses more on the relationship between cybersecurity and data protection as well as the development of cyber-resilient systems that not only prevent attacks but also ensure rapid recovery after security incidents.

What Are the Core Components of the NIST Cybersecurity Framework?
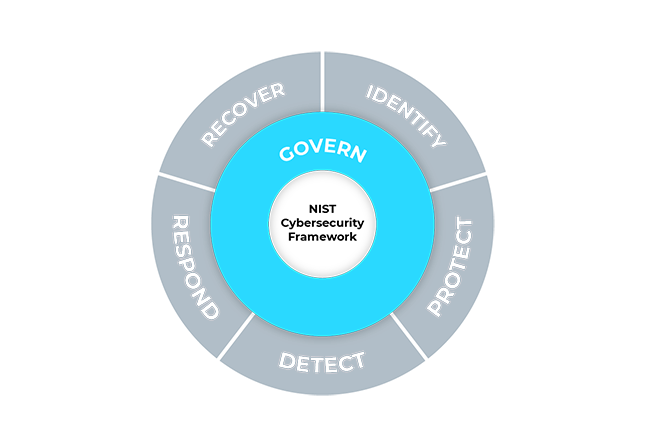
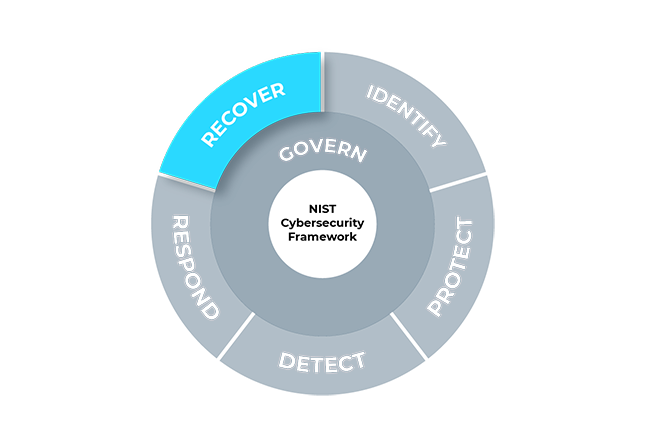
The core of the framework defines six central functions that cover the entire cybersecurity management lifecycle.
Govern
The organization’s cybersecurity risk management strategy, expectations and policy are established, communicated and monitored.

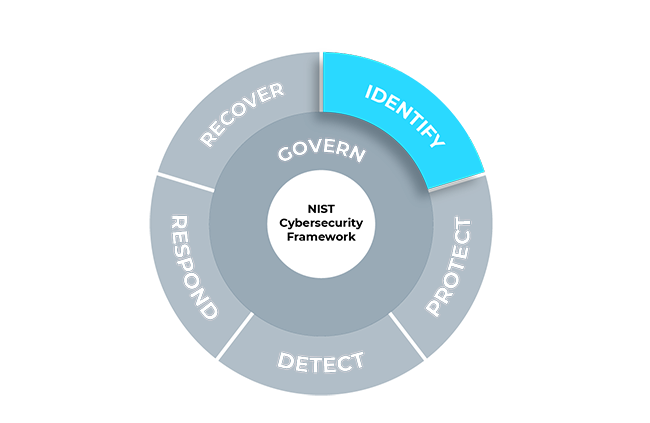
Identify
The organization’s current cybersecurity risks are understood.

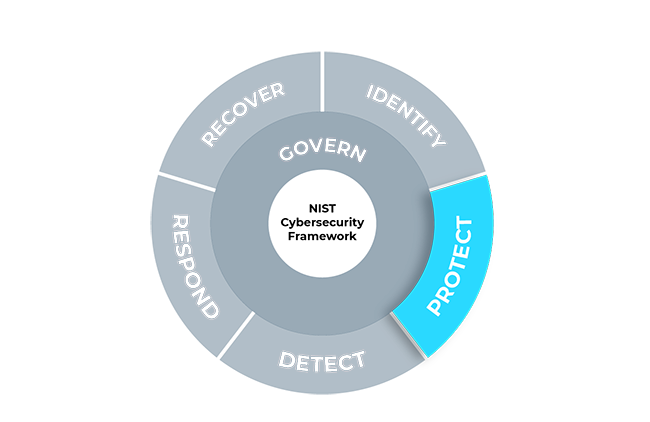
Protect
Safeguards to manage the organization’s cybersecurity risks are used.

Detect
Possible cybersecurity attacks and compromises are found and analyzed.

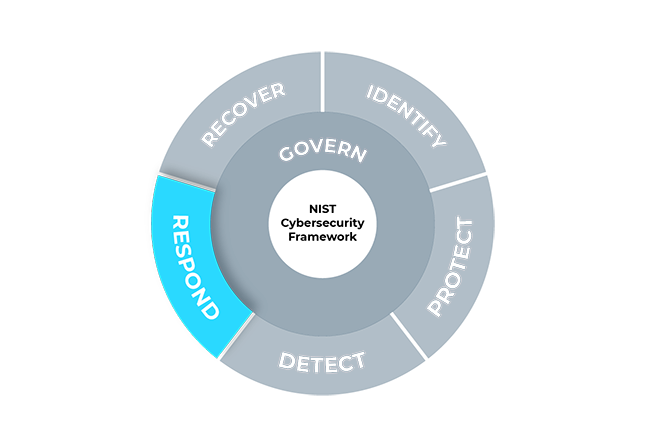
Respond
Actions regarding a detected cybersecurity incident are taken.
Recover
Assets and operations affected by a cybersecurity incident are restored.
The six functions are divided into 22 categories and more than 100 subcategories that describe specific cybersecurity activities and results. These are formulated to be understood by a wide audience with varying levels of cybersecurity expertise - from IT managers to CEOs. Because the outcomes are sector-, country- and technology-neutral, they provide an organization with the flexibility needed to address their unique risks, technologies and mission considerations.
The Security-as-a-Service solutions from Myra provide reliable protection for your IT infrastructure and web applications against cyberthreats. Ensure the security of your critical business processes proactively, sustainably and legally compliant.
06
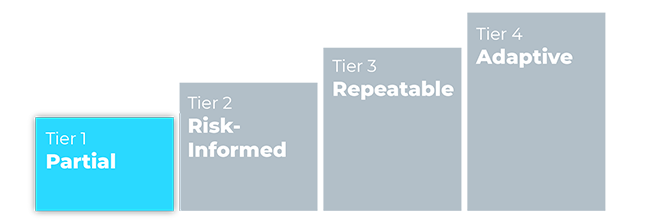
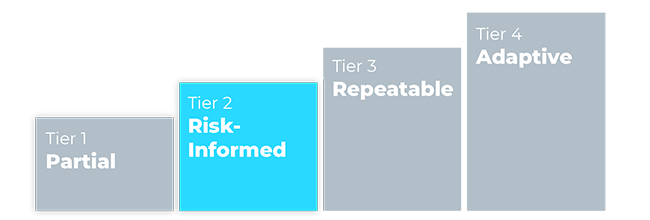
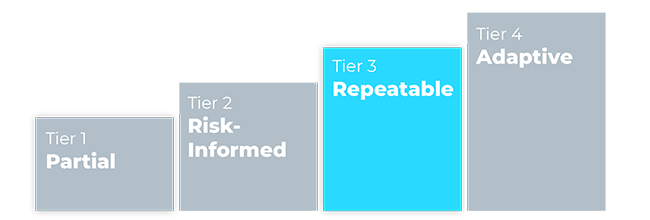
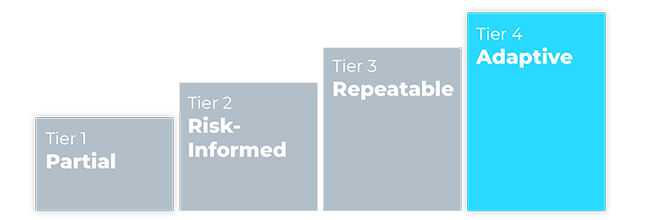
What Tiers Does the NIST CSF Include?
The NIST Cybersecurity Framework includes four tiers that can be applied to organizational profiles. These tiers provide a framework for organizations to assess the current maturity of their cybersecurity practices and set goals for improvement. The tiers are defined as follows: