Discover how Myra combines digital sovereignty and cyber resilience.
Home>
IT compliance
03
Who needs IT compliance?
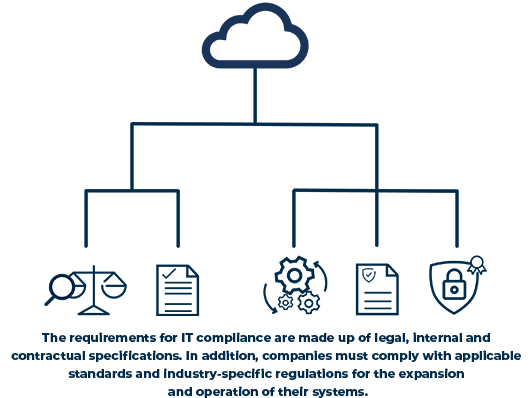
All private companies, the public sector, and all other organizations must adhere to IT compliance requirements. The law and supervisory authorities specify which requirements each company must fulfill in its specific industry. This results in the compliance requirements that must be observed. The requirements for IT and processes vary greatly depending on the industry, company size, number of customers, and overall societal importance. The strictest compliance requirements apply to critical infrastructure in the sectors of energy, healthcare, government and administration, food, transport and traffic, finance and insurance, information technology and telecommunications, media and culture, and water supply.
Especially in larger companies, compliance requirements often prove to be so extensive that a dedicated IT compliance management department is required for proper implementation. In many cases, compliance with the applicable regulatory requirements is subject to random checks by supervisory authorities. Some companies are even required to regularly demonstrate through appropriate means that all IT compliance requirements are being properly met – for example, through reports from external auditors and penetration tests.
04
What laws and standards shape IT compliance?
Most compliance requirements stem from legal bases or official regulations. The most well-known regulations for companies and other organizations include:
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) is a European Union regulation that has uniformly regulated the processing of personal data since May 25, 2018. The regulations apply to all private companies and public bodies that process the personal data of EU citizens, regardless of whether the respective organization is from the EU or another economic area. Innovations such as the right to be forgotten and the right to data portability are intended to strengthen the protection of privacy.
BSI Act (BSIG)
The BSI Act (BSIG) defines the remit of the German Federal Office for Information Security (BSI). As a top federal government agency, the BSI pursues the self-defined goal of maintaining cybersecurity “through prevention, detection and response for the nation, the economy and the public.” By defining established minimum standards, best-practice models, and mandatory regulations, the BSI provides guidance for the secure digitalization of large and small organizations. Among other things, the BSIG (Section 8a) includes requirements for critical infrastructures that stipulate the implementation of suitable security technologies for maintaining the “availability, integrity, authenticity and confidentiality of their information technology systems, components or processes.”
IT Security Act (IT-SiG)
As an amending law, the IT Security Act (IT-SiG) amends and supplements existing legislation from the BSI Act, the Energy Industry Act, the Telemedia Act, the Telecommunications Act, and other laws. One of the core objectives of the IT Security Act is to improve the security and protection of IT systems and services, particularly in the area of critical infrastructures. For these, the law provides for an obligation to report significant IT disruptions to the BSI.
ISO 27001 & ISO 27001 on the basis of IT-Grundschutz (IT baseline protection)
ISO 27001 and ISO 27001 based on IT-Grundschutz (IT baseline protection) define a framework and describe a concept for implementing an information security management system (ISMS). ISO 27001 specifies the requirements for setting up, implementing, operating, monitoring, evaluating, maintaining, and improving a documented ISMS in terms of general business risks. The international standard takes a top-down approach, focusing on processes and implementing the necessary security measures on the basis of an individual risk analysis. Developed by the BSI, ISO 27001 based on IT-Grundschutz describes a systematic method for identifying and implementing the necessary IT security measures in companies in order to achieve a moderate, appropriate, and adequate level of protection. Following a bottom-up approach, the focus is on specific measures to secure IT systems.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.