Our WAF has a new user interface – for more intuitive and efficient use. Learn more
Home>
Cybercrime
03
What forms of cybercrime are there?
In general, a distinction is made in cybercrime between crimes that are carried out entirely in the digital realm and offenses in which the network serves as a tool. While a DDoS attack, for example, is aimed at restricting the availability of web services and thus takes place entirely in cyberspace, the trade in prohibited or stolen goods can also be carried out in a completely analog way - in this case, only the transaction is carried out on virtual platforms in the darknet.
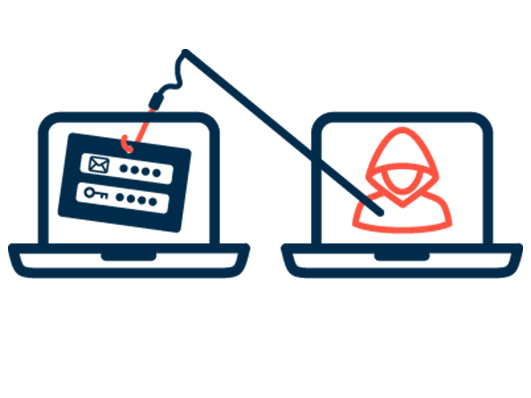
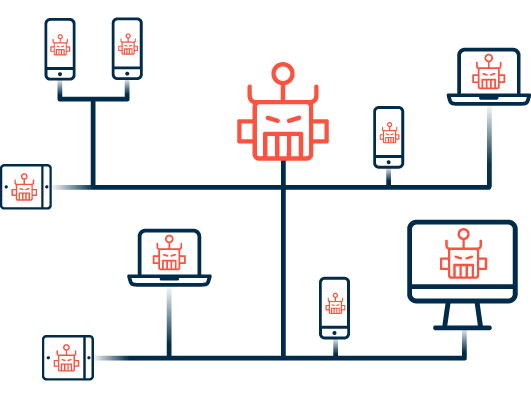
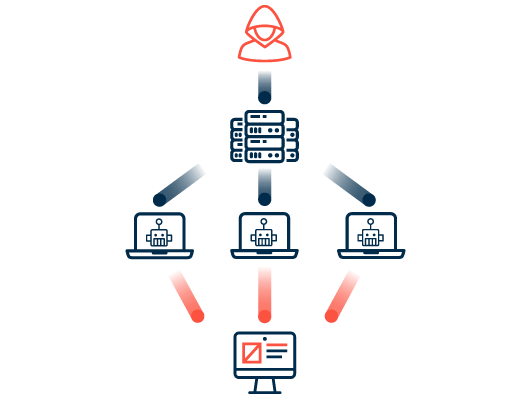
Common attack practices used by cybercriminals include:
04
Which industries are affected by cybercrime?
In general, every company is a potential target for cybercriminals, regardless of industry or size. The question is not whether, but when and to what extent an attack on one's own company takes place. Cyber criminals focus particularly on e-commerce companies, banks, FinTechs, insurance companies, the manufacturing industry, the media and the healthcare sector. However, data centers as well as authorities and other organizations from the public sector are also among the preferred targets of attackers. In 2022, almost 9 out of 10 of all German companies (84 percent) were victims of digital sabotage, data theft or espionage, according to a representative survey by the digital association Bitkom.
05
How can companies protect themselves?
To successfully combat cybercrime, companies should first observe and cleanly implement the industry-standard guidelines for data protection and IT security. Depending on size and environment, different guidelines apply here. While financial service providers, for example, are bound by the requirements of BaFin, operators of critical infrastructures are subject to the requirements of IT-SiG 2.0. In general, it is important for all companies to protect critical data sets from unauthorized access and to use backups to protect against possible data breaches. In addition, the GDPR provides for particularly careful handling of personal data.
In addition to compliance and data protection, companies must of course also keep an eye on IT security to secure their digital business processes in the best possible way. To be able to respond appropriately to increasingly complex attacks, intelligent and dynamic protection solutions are required to identify, categorize and mitigate threats independently.
These protection systems must be implemented for all relevant network layers. In the case of a managed cloud service, the service provider can, if desired, take over the complete configuration and oversee the correct operation – for example, of the DDoS protection for data centers (layer 3/4) as well as web applications (layer 7).
As part of a holistic security strategy, companies should establish organizational prevention measures in addition to technical ones. For example, it is advisable to identify target systems that are under threat as a preventive measure, clarify internal responsibilities, regulate communication with the Internet service provider, define checklists and processes for the event of an attack, and provide regular training for employees.
Cybersecurity Solutions by Myra

DDoS Protection
Myra DDoS Protection provides you with fully automatic protection against malicious requests and overload attacks. Even in the event of an imminent attack, your web applications stay available at all times.

Hyperscale WAF
The Myra Hyperscale WAF protects your web applications against malicious access and vulnerability exploits. Thanks to simple integration and configuration, it can be set up in no time at all.

CDN
First-class user experience thanks to fast page loading and minimal latency: With the Myra High Performance CDN, all static and dynamic content on your website is delivered with high performance.
Secure DNS
Myra Secure DNS offers you a reliable and powerful solution for securing your critical web applications. Manage your name resolution with ease and protect yourself against DNS hijacking.
Deep Bot Management
Say goodbye to malicious bots forever. Myra Deep Bot Management creates unique fingerprints for each bot and thus enables an optimal response to every request.
Certificate Management
No more problems with expired SSL/TLS certificates. Increase the security of your digital assets with Myra Certificate Management and encrypt all your domains automatically.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.