Our WAF has a new user interface – for more intuitive and efficient use. Learn more
Home>
BAIT
At one
look
- 01. A definition of BAIT
- 02. What do the BAIT contain?
- 02.1 IT strategy
- 02.2 IT governance
- 02.3 Information risk management
- 02.4 Information security management
- 02.5 Operational information security
- 02.6 Identity and access management
- 02.7 IT projects and application development
- 02.8 IT operations
- 02.9 Outsourcing and other external procurement of IT services
- 02.10 IT service continuity management
- 02.11 Managing relationships with payment service users
- 02.12 Critical infrastructure
- 03. What is the impact of BAIT on cybersecurity?
- 04. What you need to know about BAIT
- 05. What makes Myra the right partner for the finance industry
02.2
IT governance
Financial institutions use IT governance as the structure to manage and monitor the operation and further development of IT systems on the basis of the IT strategy, including the related IT processes. IT governance as defined by BaFin comprises:
Establishment of a structure for managing and monitoring related to the operation and further development of the IT systems and related IT processes
Responsibility for effective implementation lies with the management.
Resources for IT operations, application development, information risk management, and information security management must be appropriate in terms of both quantity and quality.
Conflicts of interest and activities that are not compatible within the organizational and operational structure of IT must be avoided.
02.4
Information security management
With an information security management system, institutions make provisions for information security and define the specific implementation in a continuous process. This results in the following requirements:
Management must adopt an information security policy in line with the strategy and communicate it within the company.
Information security guidelines and information security processes define in detail the agreed information security policy and specify measures in line with the state-of-the-art for meeting the protection objectives.
Information security processes include sub-processes, such as for identification, protection, detection, response, and recovery.
An information security officer must be appointed by management. The information security officer monitors, coordinates, and checks: information security processes, the implementation of measures, compliance, and information security incidents. In addition, duties include initiating and updating the information security policy and regular status reports to management.
Continuous and appropriate information security awareness and training programs must be established for the staff.
02.5
Operational information security
The information security management requirements are implemented in operational information security. The objective is to ensure the integrity, availability, authenticity and confidentiality of data at the system and process level and in other components of the information network. For this purpose, operational information security measures and processes such as vulnerability management, network segmentation and control, system hardening, encryption, multi-level protection concepts as well as perimeter protection must be implemented.
Furthermore, the requirements for operational information security provide for continuous logging and documentation of security-relevant events or failures. Automated systems are recommended for continuous and detailed data analysis. A permanently staffed Security Operations Center (SOC) may be required for timely analysis and response. To track the effectiveness of the measures taken, institutions must also regularly review the security of IT systems using variance analyses (gap analysis), vulnerability scans, penetration tests, simulations of attacks, and similar methods.
02.8
IT operations
The task of IT operations is to cover the requirements resulting from the business strategy as well as from the IT-supported business processes. This requires continuous and detailed recording of the inventories of all IT components, including configuration data, support and warranty details, information on protection requirements, and acceptable downtimes. Institutions are required to regularly update their inventory of IT systems. As part of lifecycle management, risks posed by outdated systems no longer supported by the manufacturer must be taken into account.
Processes for changes to IT systems must be designed and implemented based on the nature, scale, complexity, and riskiness. This includes newly procured or replaced systems as well as maintenance and security patches. Any changes to IT must be documented, evaluated, prioritized, approved, coordinated, and safely implemented by those responsible. Secure implementation includes, but is not limited to, risk analysis, data backups for the systems concerned, testing of changes and patches prior to going live, as well as recovery plans and restoration options in the event of potential problems.
Disruptions and incidents occurring in IT operations must be recorded, evaluated, and communicated accordingly (e.g., to management or the responsible supervisory authorities) depending on their extent. In addition, process-driven root cause analysis should be used to track the events that occurred and initiate the necessary actions to resolve the incident.
The requirements for IT operations also include specifications for data backup, which are to be set out in a data backup strategy. Here, the requirements for availability, readability, and timeliness of customer and business data, as well as for the IT systems required for their processing, are specified.
It is also up to the institutions to determine the current performance and capacity requirements of the IT systems and to forecast future needs.
02.9
Outsourcing and other external procurement of IT services
The BAIT define IT services as all forms of IT procurement. The outsourcing of IT services must be done in accordance with the requirements of MaRisk AT9 – financial services that the respective institution itself typically provides are considered to be outsourced. This also encompasses cloud services such as the provision of computing power, storage, platforms, or software via networked interfaces. In all cases, the outsourcing of IT services is based on a risk assessment, the nature and scope of which are defined by the institution itself.
Other outsourcing of IT services must also be managed and monitored in line with the business strategy, taking the risk assessment into account. Measures derived from risk management must be contractually agreed. These include arrangements relating to information risk management, information security management, contingency management, and IT operations. In addition, necessary exit and alternative strategies must be developed to respond appropriately to the failure of the service provider or a change of provider. The involvement of subcontractors must also be contractually arranged. The relevant risk assessment must be reviewed and amended regularly and on an ad hoc basis.
02.12
Critical infrastructure
The requirements in module twelve are directed specifically to operators of critical infrastructure according to the BIS Act (BSI-KritisV). In it, BaFin expands the BAIT to include special requirements that serve to achieve the critical infrastructure protection (CIP) objectives with regard to security of supply. Critical services in the finance sector include cash supply, card-based payment transactions, conventional payment transactions, and the clearing and settlement of securities and derivatives transactions.
According to the BAIT, institutions relevant to critical infrastructure must clearly tag critical infrastructure components within the information domain to include the relevant interfaces, in a configuration management database (CMDB) for example. In this area, too, the BAIT requirements and other supervisory regulations must be fully applied. In addition, institutions must observe the CIP objective in information risk and information security management and adopt appropriate measures to achieve this objective. In particular, appropriate mitigation measures must be taken for risks in accordance with state-of-the-art technology.
When cooperating with service providers, it must be ensured that the CIP objective also complies with the requirements of the KWG, MaRisk, and BAIT when services are outsourced. In addition, measures must be taken as part of emergency preparedness planning to ensure that institutions can allow critical services to be maintained even in an emergency situation.
Institutions must provide verification to the BSI at least every two years that the necessary measures to protect critical services have been properly taken. Verification can be provided as part of the annual audit.
04
What you need to know about BAIT
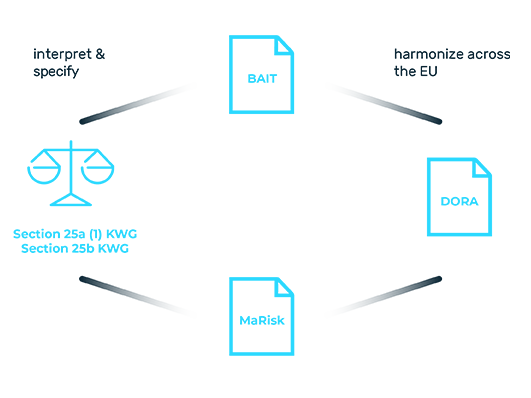
The Supervisory Requirements for IT in Financial Institutions (BAIT) set out a binding set of rules for safeguarding IT in the finance industry. Like MaRisk, the BAIT also define the statutory requirements of Section 25a KWG. The objective of the regulatory requirements is to secure the IT systems of German banks in an efficient and forward-looking manner and to set high standards for cyber resilience. In addition, the BAIT are intended to promote company-wide IT risk awareness in the institutions themselves and with respect to outsourcing service providers. In twelve modules, the BAIT cover the key areas of operational IT, the specific management and control of processes and service providers, as well as strategic governance. This gives banks a practical framework for managing and operating their IT systems and for ensuring efficient and secure interaction with affiliated partners. The latter must meet the same high standards as the banks themselves. Outsourcing is, therefore, a significant challenge, particularly in the case of material outsourcing, which only experienced service providers can manage.
As a specialist service provider for cybersecurity in the financial sector, Myra Security has long provided support for material and non-material outsourcing in accordance with KWG Section 25, MaRisk AT 9, and BAIT. With our expertise, we fully support banks in outsourcing and contingency management. Compliance is our day-to-day business. Our Security Operations Center (SOC) monitors all systems and events 24/7. Prestigious companies and organizations from the financial industry have been using Myra’s Security-as-a-Service platform for years to cover both their cybersecurity and compliance needs.
05
What makes Myra the right partner for the finance industry
GDPR-compliant specialist provider with industry expertise (Sparkassen-Finanzportal, DSV IT Service, savings banks and direct banks, financial service providers, critical infrastructure)
Investment-secure technology: fully automated attack mitigation, high-performance delivery, maximum scalability
Audit-proof: Myra meets all requirements for material outsourcing according to Section 25b of the Banking Act (KWG), MaRisk AT9, and BAIT.
Myra already meets all of the requirements of the planned EU Digital Operational Resilience Act (DORA) for risk management, reporting, testing, and outsourcing.
Maximum certified quality: ISO 27001 based on IT-Grundschutz (IT baseline protection), PCI-DSS certified, BSI-KRITIS certified, BSI C5 attestation (in progress), Trusted Cloud
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.