Visit us at it-sa in Nuremberg from October 7 to 9. Get your free ticket now!
Home>
5G
02
How does 5G work?
The 5G technology available to date usually still requires an existing 4G network to establish a connection, so it does not work independently. That is why this is referred to as 5G non-standalone (5G NSA). The full potential of 5G will only be exploited with independent networks (5G standalone, 5G SA), upgraded technology behind the transmission towers, and compatible devices.
03
What are the advantages and disadvantages of 5G?
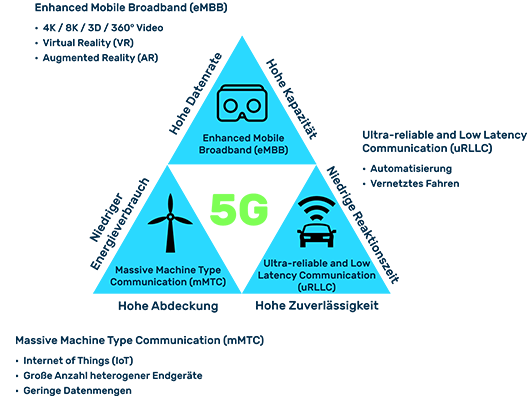
Theoretically, 5G technology enables data rates of up to 20 Gbit/s and thus up to 20 times faster data transmission than the previous generation. At the same time, 5G promises latency times of less than one millisecond, which for the first time allows data communication in real time. Energy consumption is also expected to be lower than with 4G, and it should be possible to network up to 1,000 times more devices per square kilometer. This opens up numerous new application possibilities in professional and private environments.
Benefits and application areas for industry and business
Improved machine-to-machine (M2M) communication for automation (e.g., wirelessly connected manufacturing robots)
Real-time communication as the basis for connected road traffic and self-driving vehicles
Guaranteed network availability (e.g., for emergency services) through service levels and private campus networks (closed 5G networks for local company sites, a university, or individual buildings)
Telemedicine (e.g., augmented reality, direct video connection, and smart meters)
Digital agriculture (e.g., remote control of agricultural machinery and the use of digital measurement and control technology)
Benefits and application areas for consumers
Shorter loading times and faster page loading (e.g., browsing or video streaming)
Very low response time (e.g., when online or cloud gaming)
Better coverage and stability of the connection (e.g., at large events or on a train)
Improved mobile telephony (voice over 5G)
Possible alternative to fixed networks for gigabit internet
New application areas such as augmented or virtual reality in real time, ultra-high-resolution live TV (5G broadcast), and 4K video telephony
Drawbacks
Gigabit mobile communications have so far provided little added value for consumers
Still inadequate availability (especially in rural areas)
More transmission antennas required for uniform network coverage than with 4G
05
What are the risks associated with 5G?
Of course, there can be no hundred percent security in the 5G network either. Security researchers have already uncovered several vulnerabilities in the network protocols that permitted man-in-the-middle attacks and DoS attacks, among other things. In general, software vulnerabilities are one of the main gateways for cybercriminals. And since software plays a significant role in the 5G infrastructure, the potential risk it poses is also immense.
Backdoors built into network components at the factory or at a later time can also pose a risk, such as permitting data to be spied on or even sabotage attacks to be carried out. In this context, there is also the risk of government interference. As one of the main suppliers of 5G components, Chinese network equipment supplier Huawei has come under criticism in many places.
The United States, for example, is accusing it of taking part in espionage on behalf of the Chinese government. For this reason, Germany’s IT Security Act (IT-SiG 2.0) provides for critical components from suppliers to be subjected to strict scrutiny and for “untrustworthy” manufacturers to be excluded from the 5G network rollout.
As the new cellular standard becomes more widespread, the impact of botnet-based DDoS attacks will inevitably increase. This is because even more IoT devices will be networked at significantly higher data rates via 5G in the future. If they are not adequately secured, cybercriminals will have far more bandwidth at their disposal, which they can misuse for more powerful attacks.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.