Our WAF has a new user interface – for more intuitive and efficient use. Learn more
Home>
HTTPS
03
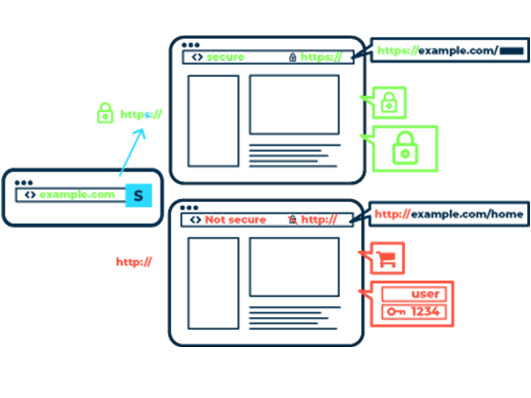
Why use HTTPS?
Although only very few online portals process highly sensitive content, an unprotected website can still pose a threat to site visitors. For example, cybercriminals use unencrypted connections to corrupt connections and distribute malware on modified websites. Man-in-the-middle attacks (MITM) are used for this purpose, in which attackers hijack the communication between the user client and the web server of the respective website and take control of the data traffic.
Such MITM attacks often form the starting point for more extensive attacks on the systems of site visitors and the underlying network. In combination with other attack vectors such as spear phishing, it is also possible to infiltrate companies, government agencies and other organizations. To counter this danger, all websites and services on the network should be consistently encrypted with HTTPS.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.