Visit us at it-sa in Nuremberg from October 7 to 9. Get your free ticket now!
Home>
Government & Government Agencies







Fortify Your Digital Defenses With Myra
4 key areas – 1 outstanding technology
Security
Avoid data theft, system outages, and disrupted communications. Our robust defense system protects your critical processes with unwavering vigilance.
Performance
Experience high-performance delivery of your content, even during traffic peaks. Maintain optimal performance and provide your users with a seamless experience.

Business Continuity
Myra ensures the utmost protection for your business by utilizing direct and geo-redundant connections to your infrastructure, without relying on external factors.
Compliance
Meet the requirements of IT security and data protection teams with ease. Myra is your trusted partner, offering unrivaled expertise in the strictest compliance regimes.
Designed and engineered for highly regulated sectors
Certified Security from Myra: Compliance Without Compromise
ISO 27001 on the basis of IT-Grundschutz (BSI)
Payment Card Industry Data Security Standard (PCI DSS)
BSI C5 Type 2
KRITIS Proof according to § 8a para. 3 BSIG
Trusted Cloud Service
IDW PS 951 Type 2 (ISAE 3402)
VS-NfD







Do you have
questions?
Please contact us via contact form or call us at:
+49 89 414141 - 345.
Protect sensitive citizen data from malicious traffic
FAQ: IT Security for Public Authorities
NIS2 attaches great importance to security in the digital supply chain. Authorities and public institutions at federal level must therefore ensure that their service providers and suppliers also comply with cybersecurity standards. This means that public administrations must not only protect their own systems and processes, but also pay attention to securing their partners and service providers to keep an eye on the entire supply chain. Against this background, the selection of reliable partners with the necessary expertise in the public sector and the corresponding evidence in the form of relevant certifications and test certificates such as ISO 27001 or BSI C5 is of great importance.
To protect themselves against cybercrime, authorities and public institutions must develop and implement a comprehensive security strategy. This strategy should include both technical and organizational measures that are tailored to the specific requirements and risks of the public sector. Key elements of this strategy include regular security audits, continuous reviews of existing protective measures and timely updates to IT systems. Equally important are targeted training and awareness-raising programs for employees at all levels and for citizens who interact with the administration's digital services. These programs help to raise awareness of cyber threats and reduce the risk of successful attacks on public infrastructure.
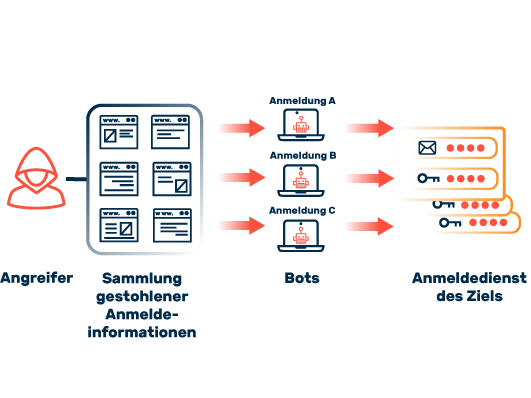
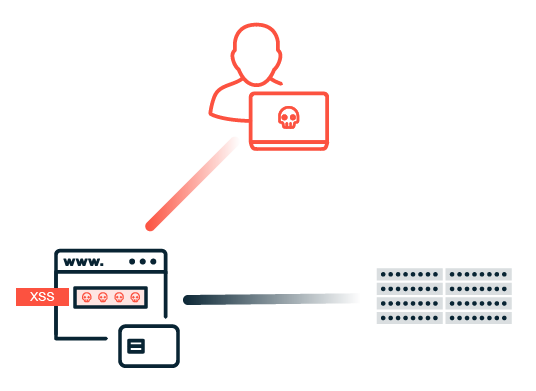
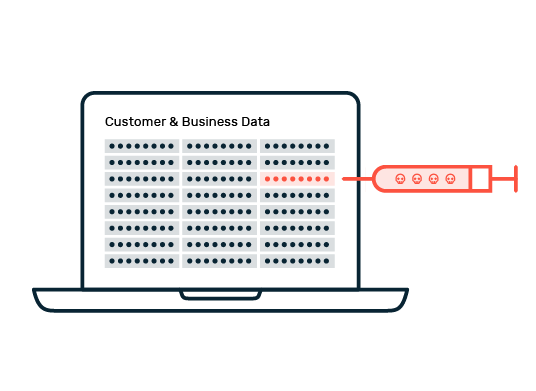
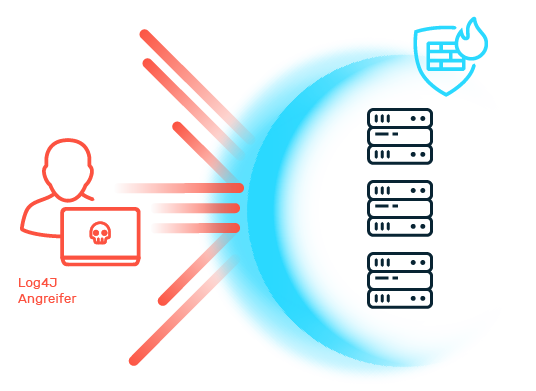
The extent to which IT security can protect public authorities from attacks essentially depends on the type of attack and the protection solutions implemented. Cybercriminals see public administration as an attractive target for various types of attacks. One of the most common threats are DoS and DDoS attacks, which can impair the functionality of government online services. No less dangerous are ransomware and phishing campaigns aimed at stealing sensitive administrative and citizen data or extorting ransoms. This data often has a considerable value on the black market. Another challenge is posed by social engineering tactics, where attackers exploit human vulnerabilities to gain unauthorized access to confidential information or commit fraud within government structures. The actual effectiveness of the IT security measures implemented in public authorities can often only be fully assessed in the event of a real cyberattack.