Discover how Myra combines digital sovereignty and cyber resilience.
Home>
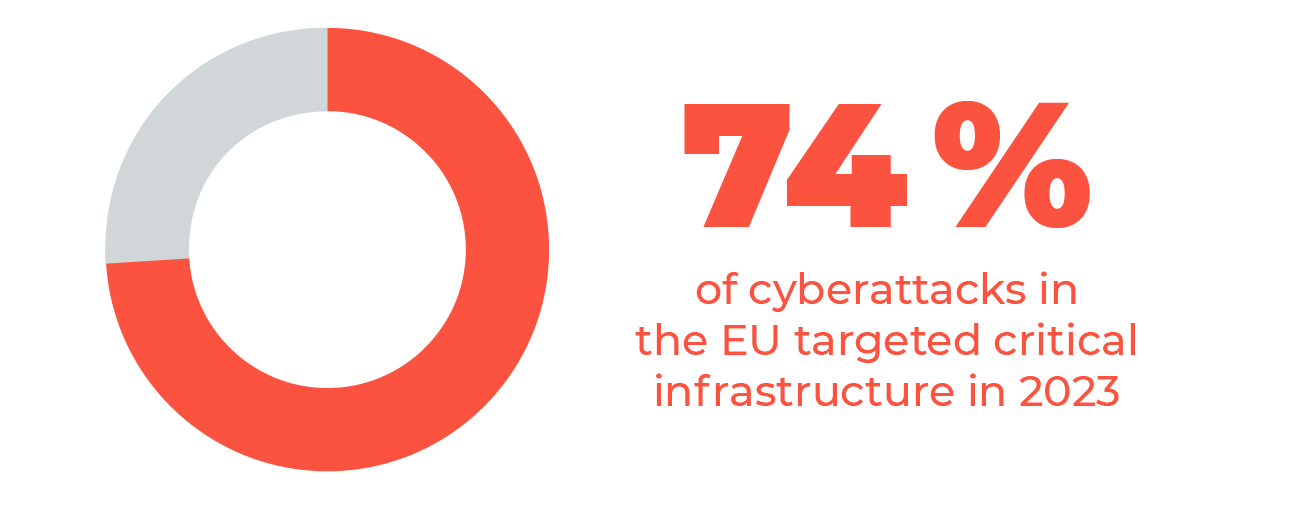
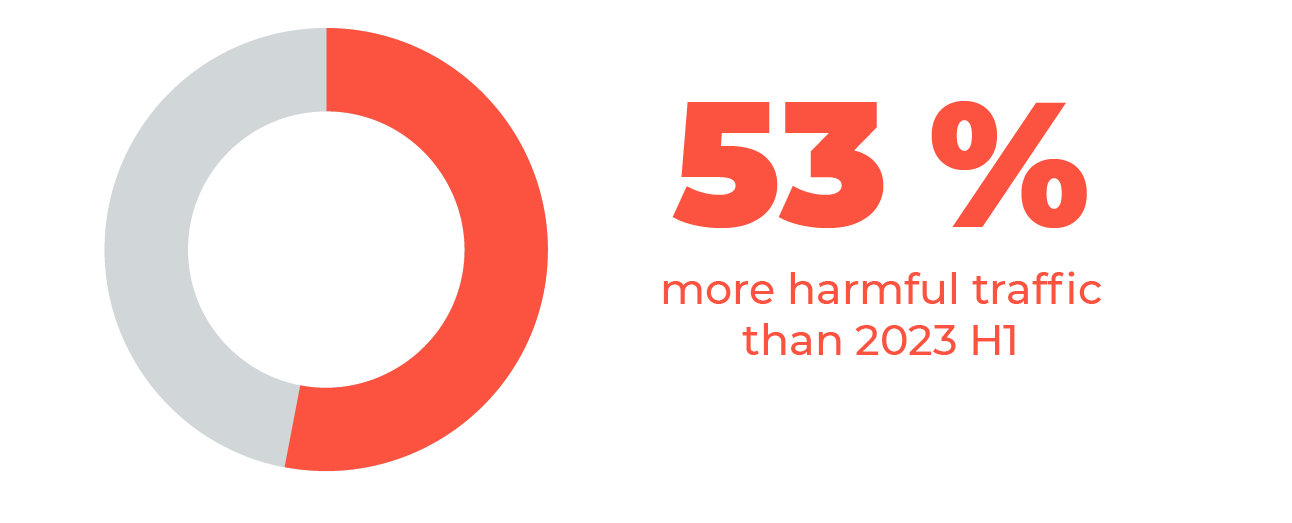
Threat Report 2024 H1
Trends & Key Insights
Expert interview with zeroBS CTO Markus Manzke on the DDoS threat (excerpt)
Markus Manzke is Chief Technology Officer (CTO) of zeroBS, a Germany-based pentesting company. zeroBS helps its customers understand and address the risks of operating Internet-based infrastructures.
(For the full interview and more information from zeroBS on the new HTTP/2 Continuation Flood attack technique, download the report now).
DNS attacks seem to be becoming more prominent, which methods are leading the way?
Since 2023, an increase in DNS flood attacks has been observed by various manufacturers. DNS servers are put under so much strain that they cease to operate and the attacked target is virtually digitally erased.
Which attack vectors cause companies the most difficulties in defending themselves?
The most successful attacks currently take place via the application layer, as this has an extremely high degree of complexity due to a combination of the attack surface (number and distribution of targets) and the technology used (classic web applications, APIs, API-generated websites).
How the Threat Report can help you
Use the data, analyses and forecasts in the report

Recognize risks
Find out which dangers threaten your business.

Derive measures
Recognize the potential of holistic protection solutions.

Close gaps
Implement tailor-made solutions to protect your digital assets.

Build resilience
Use the business continuity you gain as a competitive advantage.