Discover how Myra combines digital sovereignty and cyber resilience.
Home>
Cross-site-scripting
01
A defintion of Cross-site scripting
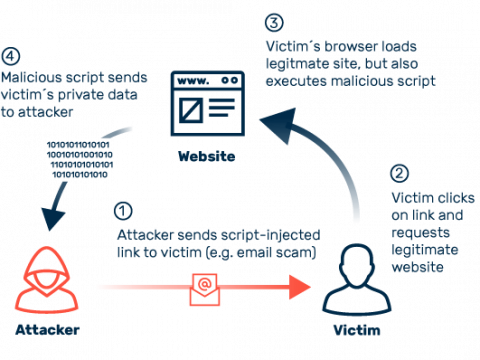
Cross-site scripting is one of the most popular vectors of attack on the internet. The reputable Open Web Application Security Project (OWASP) even lists XSS among the top 10 threats of the most critical security risks for web applications. Attackers use cross-site scripting to inject malicious script code into web pages that are normally harmless and trustworthy. When a user visits such a page and logs in using his login data, the attackers can access parts of the session or even completely take over the login process. The severity of the attack varies depending on how privileged the browser treats the affected web application. In the worst case, attackers gain extensive access rights to the user’s system and may even be able to access local data. A complete takeover of the affected system is also possible via XSS. Other XSS-based types of attacks include phishing and “website defacement.” With the latter, attackers put content on a web page for purposes of defamation without the site operator being aware of it.
02
Types of cross-site scripting
In practice, there are three types of XSS: non-persistent (or reflected) cross-site scripting, persistent (or stored) cross-site scripting, and local (or DOM-based) cross-site scripting. Common to all of them is that attackers use malicious script code in widespread languages such as JavaScript for their attacks.
04
Protective measures against XSS attacks
Due to the varying forms of XSS attacks, this vector of attack affects companies and website operators, as well as their customers and users. Consequently, the protective measures for defending against XSS attacks must be correspondingly wide-ranging.
Client-side protection against XSS
Users can protect themselves against XSS attacks by restricting the processing of script code in their browsers. A variety of add-ons, such as NoScript, can be used for script management in browsers. However, for most users, this proactive management is likely to be too unwieldy – constant adjustments are required to ensure that web applications continue to work correctly. For this reason, extensions of this kind are rarely used in practice.
As a general rule, it is advisable to always carefully examine links in incoming emails for conspicuous snippets of code. For safety’s sake, when in doubt, the address of the particular page should be entered manually to access it. If possible, HTML should be avoided when viewing emails in the client – plain text is perfectly suited for digital communication. This is an effective way to fend off maliciously manipulated links in e-mails.
Server-side protection against XSS
Protective measures against XSS are more extensive on the company side. Strict code guidelines and input checks, for example, can help webmasters to minimize the attack surface for XSS attacks. Whitelisting also enables site operators to define harmless input and, conversely, prevent the transmission of malicious script code to the server. In practice, depending on the web application, this approach is very complex and, consequently, sometimes flawed. If inadequately configured, whitelisting also blocks legitimate user input, impairing the functionality of the web application.
A WAF (Web Application Firewall) can remedy the situation. The security solution filters incoming traffic based on predefined rules, differentiating between legitimate user requests and potential attacks. The technology’s protection factor is based primarily on the correct configuration of filter rules – this requires expertise and knowledge of the kind of traffic on the specific web application.
05
Cross-site scripting: What you need to know
XSS attacks have been part of the standard arsenal of cybercriminals for quite some time, and this will not be changing in the foreseeable future. For attackers, XSS constitutes a lucrative method for carrying out extensive phishing campaigns via spam. Sensitive access data and account information are enticing spoils. Furthermore, XSS makes it possible to take over active login sessions as well as access local systems. Also on the attackers’ agenda is the defamation of companies by defacement. For example, anyone who succeeds in sneaking obscene content onto the website of a reputable bank will cause long-term damage to its image.
XSS affects companies, customers, and users alike. That is why rigorous protection of web applications should be a top priority for webmasters. User input must be thoroughly checked to prevent malicious code from reaching web servers in the first place. A further layer of defense is rigorous whitelisting of the permitted input patterns, but this can be a very time-consuming process.
Myra Application Security with WAF, Bot Management, and DNS offers equally reliable and flexible protection against XSS attacks and many other types of attack.
To Myra Application Security