Discover how Myra combines digital sovereignty and cyber resilience.
Home>
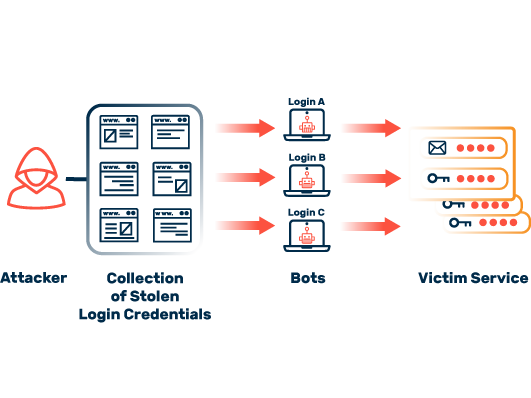
Credential Stuffing
What are the consequences of credential stuffing?
An attack via credential stuffing always harms the affected companies and institutions. Victim organizations still suffer from the consequences even years later. It is, therefore, extremely important to have effective protection.

Economic losses
Online retailers incur additional costs when customers discover that their credentials have been misused. For example, increased refunds result in a heavy economic burden.

Image loss
If user data is misused or stolen on your end, this will negatively affect the relationship with your customers. Regaining trust could take years and require enormous investments.

Data manipulation
If attackers gain access to your users’ data, they will be able to change and manipulate it at will. The longer such data misuse remains undiscovered, the greater the damage can become.
05
How can companies protect themselves from credential stuffing?
It is extremely challenging for the affected companies to defend themselves against credential stuffing. A balancing act of security and usability is called for here. Complex password security requirements and downstream human interaction verification mechanisms such as captchas increase the security of websites. However, if they are configured too aggressively, they can cause user frustration.
Also, captchas do not pose an insurmountable hurdle for attackers. Specialized service providers have long since established themselves on the internet, working with an army of low-paid workers to solve captcha challenges at ridiculously low prices, and API connections to these questionable services are also available. In this context, a simple extension of existing attack tools is all that is needed to circumvent captchas.
Another and much more effective method of fighting against bots is the systematic control of automated requests. Malicious bots are clearly identified and blocked using special software. At the same time, harmless requests, from search engines, for example, are still tolerated. Since about half of all current website traffic consists of bot requests, the management of these data streams has enormous potential.
Myra protects your web services from credential stuffing
With Application Security and its integrated Bot Management, Myra Security offers an upstream protection instance that protects web applications from credential stuffing. High-performance Myra technology monitors, analyzes, and filters malicious internet traffic before virtual attacks cause any real damage.
About Myra Application Security