Our WAF has a new user interface – for more intuitive and efficient use. Learn more
Home>
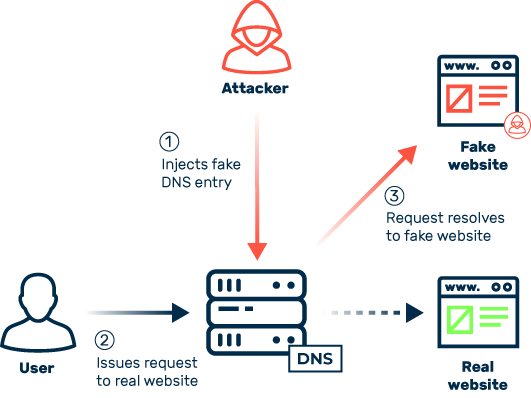
Cache Poisoning
03
What impact does DNS cache poisoning have on businesses?
Cybercriminals can use cache poisoning to target the customers of individual companies and services. Such attacks have serious consequences for the companies involved:
Operating losses
Customers are kept away from their platform and are unable to make purchases. If abuse is caused by stolen access credentials, additional costs are incurred, as the number of refunds increases, for instance.
Image loss
Although the problem usually does not lie with the affected companies themselves, attacks using cache poisoning do have an impact on their image. For customers it makes no difference who is actually responsible. They directly attribute the data breach to the provider’s lack of digital competence.
Data manipulation and misuse
If customer data is corrupted as a result of cache poisoning attacks, this can also result in major losses. Especially if tampering remains undiscovered for a long time, high follow-up losses threaten to occur—sometimes for the time-consuming job of cleaning of the data.